Ankündigungen
Trust Wallet Browser Extension v2.68 Incident: An Update to Our Community
Beitrag teilen
Wichtigste Punkte
A work-in-progress update on the Browser Extension v2.68 incident

Transparency and user trust are core to Trust Wallet. We are sharing a work-in-progress update on what we know about the incident so far, the actions we’ve taken, and what affected users should do next.
Before getting into the details, we want to say this clearly: we deeply regret the loss, concern, and disruption this incident has caused. We understand the severity of the situation, and we recognize how unsettling it has been for many in our community.
From the moment we became aware of the security incident, teams within Trust Wallet mobilized immediately and have been working around the clock to contain the incident, prevent further losses, support affected users, and thoroughly investigate what led to it. Protecting our users and preventing additional harm has been and remains our highest priority.
Additionally, we view this incident not only as a critical lesson for Trust Wallet, but as a potential inflection point and lesson for the broader industry on evolving supply chain attacks.
What happened
On December 24, 2025, an unauthorized and malicious version of the Trust Wallet Browser Extension (version 2.68) was published to the Chrome Web Store outside of our standard release process (without mandatory review). This version contained malicious code that, when loaded, allowed the attacker to access sensitive wallet data and execute transactions without authorization.
Scope and impact
Based on our investigation, this security incident affects:
Only Trust Wallet Browser Extension version 2.68 users who opened the extension and logged in during the affected period of December 24-26, 2025.
If you have received an app push via the Trust Wallet mobile app or you see a security incident banner on your Trust Wallet Browser Extension, you may still be using the compromised wallets.
Please note that it does NOT affect:
Any Trust Wallet mobile app users
Users on any other Browser Extension versions during the affected period
Browser Extension v2.68 users who opened and logged in after December 26, 2025 at 11:00 UTC.
Users who do not see the security incident banner on their Trust Wallet Browser Extension.
We have identified 2,520 wallet addresses that were affected by this incident and drained by the attackers, with approximately $8.5 million in assets impacted that can be associated with 17 wallet addresses controlled by the attacker. It is important to note that we found that these attacker addresses also drained wallet addresses NOT associated with Trust Wallet and this incident. We are actively tracking other wallet addresses that may have been impacted and will release updated numbers once we have confirmation.
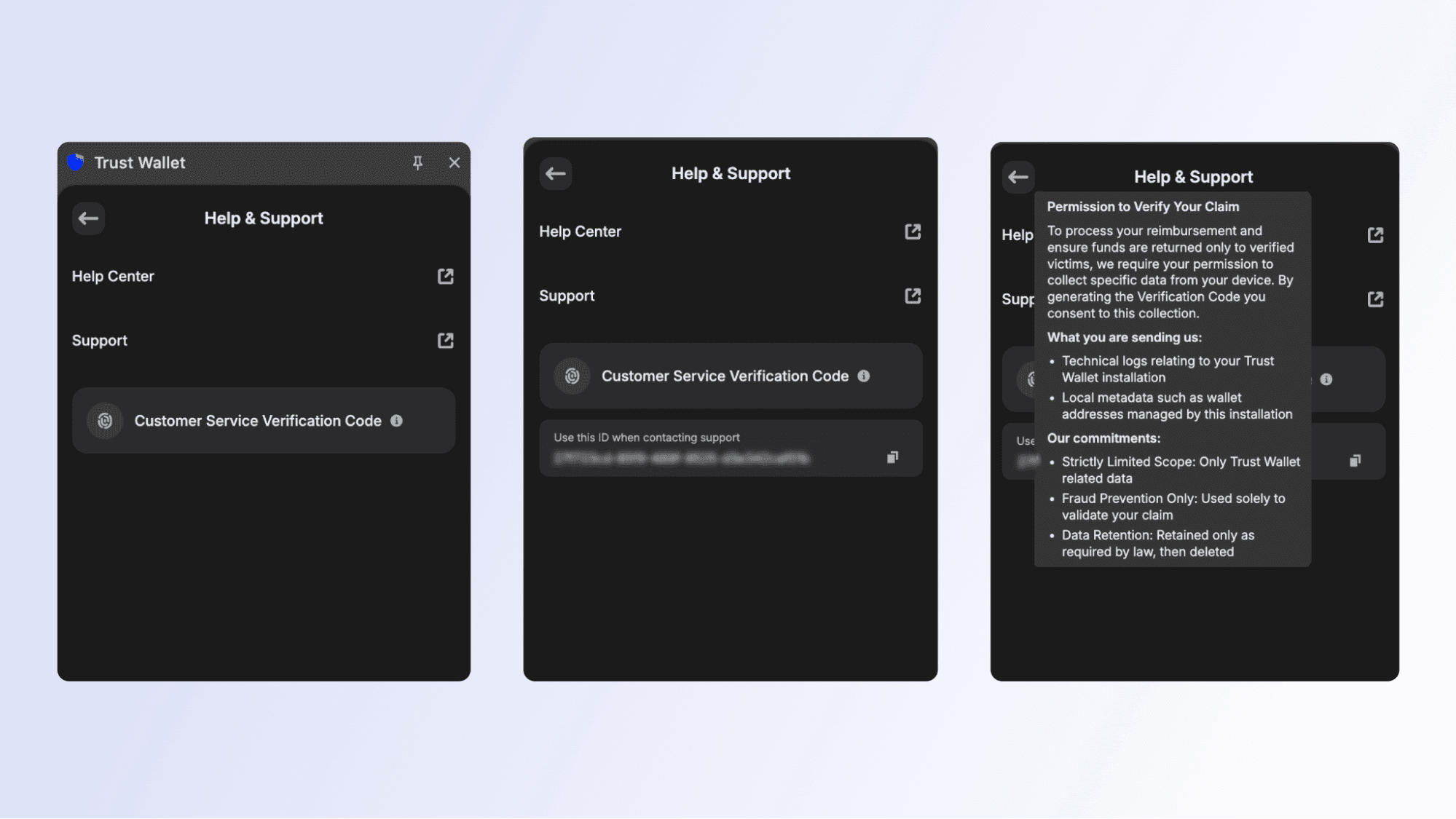
Trust Wallet has decided to voluntarily reimburse the affected users. We are finalizing the reimbursement workflow and ownership verification process, and have already started working with victims that have contacted us over the past few days.
What affected users should do
If you used Trust Wallet Browser Extension v2.68 during the affected period and logged in to your wallet:
Transfer your funds from any at-risk wallets to a newly created wallet following these instructions
Submit your reimbursement claim through our official support form: https://be-support.trustwallet.com
Please be cautious of impersonators and refer to official channels. Trust Wallet will never ask for your private keys, seed phrases, or passwords.
We recognize how stressful this may be for affected users. We ask for your patience as the team carefully reviews all submissions. If you have been impacted and submitted the form, it's critical to ensure the privacy of your case and interact only with the official Trust Wallet support.
Reimbursement process and status
Following confirmation of the incident, and after providing actions the affected users could take to safeguard their funds from additional attacks, we initiated the reimbursement claim process for the victims.
We’ve identified 2,520 affected wallet addresses that were verifiably associated with Trust Wallet browser extension users at the time of the incident. In parallel, we have received over 5,000 claims, indicating a significant number of duplicate or false submissions likely attempting to take victims’ reimbursements.
Because of this, accurate verification of wallet ownership is crucial to ensure funds are returned to the victims and not bad actors. As seen in similar incidents across the industry, there is no method that can provide absolute certainty to distinguish victims from bad actors. We have to tread cautiously, and we are working on a "best-effort" basis to design and implement a rigorous and auditable verification process.
Our team is working diligently to verify claims; combining multiple data points to verify claim legitimacy. Claim reviews are ongoing and handled on a case-by-case basis. Due to the complexity of verification and the need to protect against fraud, processing times vary with each case. We will continue to provide updates as claim reviews progress.
We are also in the process of expanding support team capacity to better handle the work involved in this process.
Incident timeline and investigation findings (so far)
So far, our investigation suggests that the malicious build of the browser extension v2.68 was prepared independently by the attacker and distributed through an external publishing method, using a leaked API key, to the Chrome Web Store.
The investigation into the exact attack vector and sequence of events remains ongoing, however, we have high confidence that the Browser Extension v2.68 incident is likely related to the industry-wide Sha1-Hulud incident in November. We believe this incident allowed the attacker to access the browser extension source code and the Chrome Web Store API key. Using that access, they were able to prepare a tampered version of the extension with a backdoor designed to collect users’ sensitive wallet data releasing the malicious version to the Chrome Web Store using the leaked (CWS) API key.
Here is a further timeline of events:
November 2025
Sha1-Hulud, an industry-wide supply chain incident, impacted multiple companies via compromised npm packages.
Our Developer GitHub secrets were exposed in the attack, which gave the attacker access to our browser extension source code and the Chrome Web Store (CWS) API key.
The attacker obtained full CWS API access via the leaked key, allowing builds to be uploaded directly without Trust Wallet's standard release process, which requires internal approval/manual review.
December 2025 - Attacker's preparation
The attacker registered domain metrics-trustwallet.com (and sub-domain api.metrics-trustwallet.com) with the intention of hosting malicious code and embedding a reference to that code in their malicious deployment of the Trust Wallet Browser Extension.
The attacker externally prepared and uploaded a tampered version of the browser extension, using the codebase of an earlier version that they had accessed through exposed developer GitHub secrets. This included the reference to the malicious code hosted on the attacker’s web domain, designed to collect users’ sensitive wallet data. This was achieved without a traditional code injection, as the attacker had direct access to the extension’s source code.
The attacker published version 2.68 on the Chrome Web Store for review using the leaked CWS key, and the malicious version was released automatically upon passing Chrome Web Store review approval, thus bypassing Trust Wallet's internal review and approval controls.
December 2025 - Incident actions
On December 25th, the first wallet-draining activity was publicly reported. 0xAkinator and ZachXBT flagged the issues and actively identified and tracked the attacker's wallet addresses, while partner Hashdit and internal systems notified us with multiple suspicious alerts.
White-hat researchers initiated DDoS attacks in an attempt to temporarily disable the attacker's malicious domain, api.metrics-trustwallet.com, helping to minimize further victims.
We rolled back to verified clean version 2.67, released as 2.69, and published urgent instructions to upgrade to the latest version to mitigate further losses.
We announced the decision to reimburse affected users, initiated the process, and continue to share updates documenting our actions. The investigations and reimbursement workflow are still ongoing.
We have already begun tightening our security measures across all fronts, including access controls, monitoring systems, release publishing process, credential management, and incident response processes.
Sha1-Hulud was an industry-wide software supply chain attack that affected companies across multiple sectors, including but not limited to crypto. It involved malicious code being introduced and distributed through commonly-used developer tooling. This allowed attackers to gain access through trusted software dependencies rather than directly targeting individual organizations.
Our commitment to security
Security is of utmost importance. In parallel with the investigation, we have actively worked on the following:
Incident response
We have already implemented additional safeguards and controls surrounding
Browser extension releases
Release system and tool access
Monitoring to prevent similar incidents
Additional security hardening
In addition, we are bringing attention to existing Trust Wallet security practices
Application publishing pipelines, dependency scanning, version control and supply-chain protections.
Global access controls, credential management, and rotation policies.
Visibility and audibility across release and publishing workflows to improve detection for anomalous activities.
Incident detection, monitoring, response, and communication processes to enable faster action and greater transparency.
How we responded and ongoing efforts
Once the incident was confirmed, our team quickly rolled back and released a clean, secure release (version 2.69). Publishing access and related API credentials were disabled, and deployment permissions were restricted as part of containment.
In parallel, we worked with blockchain analytics partners and the security community to track fund movements and support affected users.
To protect users from confusion or unsafe behaviors, we prioritized replacing the vulnerable browser extension with a safe version before making a public announcement. So affected users could update securely while minimizing their potential exposure to the hack and lost funds. Once the secure version v2.69 was available, we promptly issued guidance and warnings around the incident.
And soon after, we decided to reimburse the affected users and began planning the reimbursement process for affected users.
And as a reminder, if you have received an app push via the Trust Wallet mobile app or you see a security incident banner on your Trust Wallet Browser Extension, you may still be using the compromised wallets. This means you have logged in to your wallet using Trust Wallet Browser Extension v2.68 during the affected period of December 24-26, 2025. Please take actions to transfer your funds from any at-risk wallets to a newly created wallet following these instructions.
We are also developing tooling to verify the reimbursement claims of affected users - a browser extension customer service verification code - to be released shortly in the Browser Extension version 2.70. The newly developed tool allows affected users to contribute an additional verification element to their case.
We appreciate all the independent researchers, white-hat contributors, and community investigators, including those who helped flag indicators and disrupt malicious infrastructure, for their efforts.
Thank you to our community for your vigilance, support, and feedback as we work through this together. We recognize the impact this incident has had on our community and the affected users, and we appreciate your patience as our team continues to investigate and execute the reimbursement process.
While our forensic investigation is still ongoing, we have seen the community’s concerns arise that our incident is an example of a new class of supply chain attacks, and we share a similar sentiment. We will continue to update and share any new findings during our investigation through official Trust Wallet channels.
We hope that by sharing our findings, we can help the wider industry to recognize and mitigate similar security risks. By coming together as an industry, we are able to make a considerable effort in protecting against further hacks and exploits.
Disclaimer: Content is for informational purposes and not investment advice. Web3 and crypto come with risk. Please do your own research with respect to interacting with any Web3 applications or crypto assets. View our terms of service.
Join the Trust Wallet community on Telegram. Follow us on X (formerly Twitter), Instagram, Facebook, Reddit, Warpcast, and Tiktok
Note: Any cited numbers, figures, or illustrations are reported at the time of writing, and are subject to change.




