Seguridad
Embedded Wallet Security: What VELLET Tells Us About DApp Safety
Compartir publicación
En resumen
Learn how embedded wallet security works, what the VELLET protocol shows us about protecting DApps, and the best practices for safe integration.

Key takeaways:
Embedded wallets make DApps easier to access but introduce risks in key management, visibility, and recovery.
The VELLET protocol demonstrates how strong cryptography, explicit consent, and secure backups can make embedded wallets safer.
DApp developers must focus on encryption, transparency, recovery options, and audits to ensure responsible integration.
Decentralized applications (DApps) need a secure and smooth way for you to interact with blockchain networks. Wallets are the entry point to these apps, enabling you to sign transactions and hold digital assets. Many DApps now use embedded wallets to make access easier by hiding the technical setup. Hiding complexity can also reduce transparency and pose real risks if security is not properly handled.
This article explains the risks connected to embedded wallets, reviews what the VELLET protocol teaches us about designing safer wallet integrations, and concludes with best practices for DApp developers to ensure stronger protection.
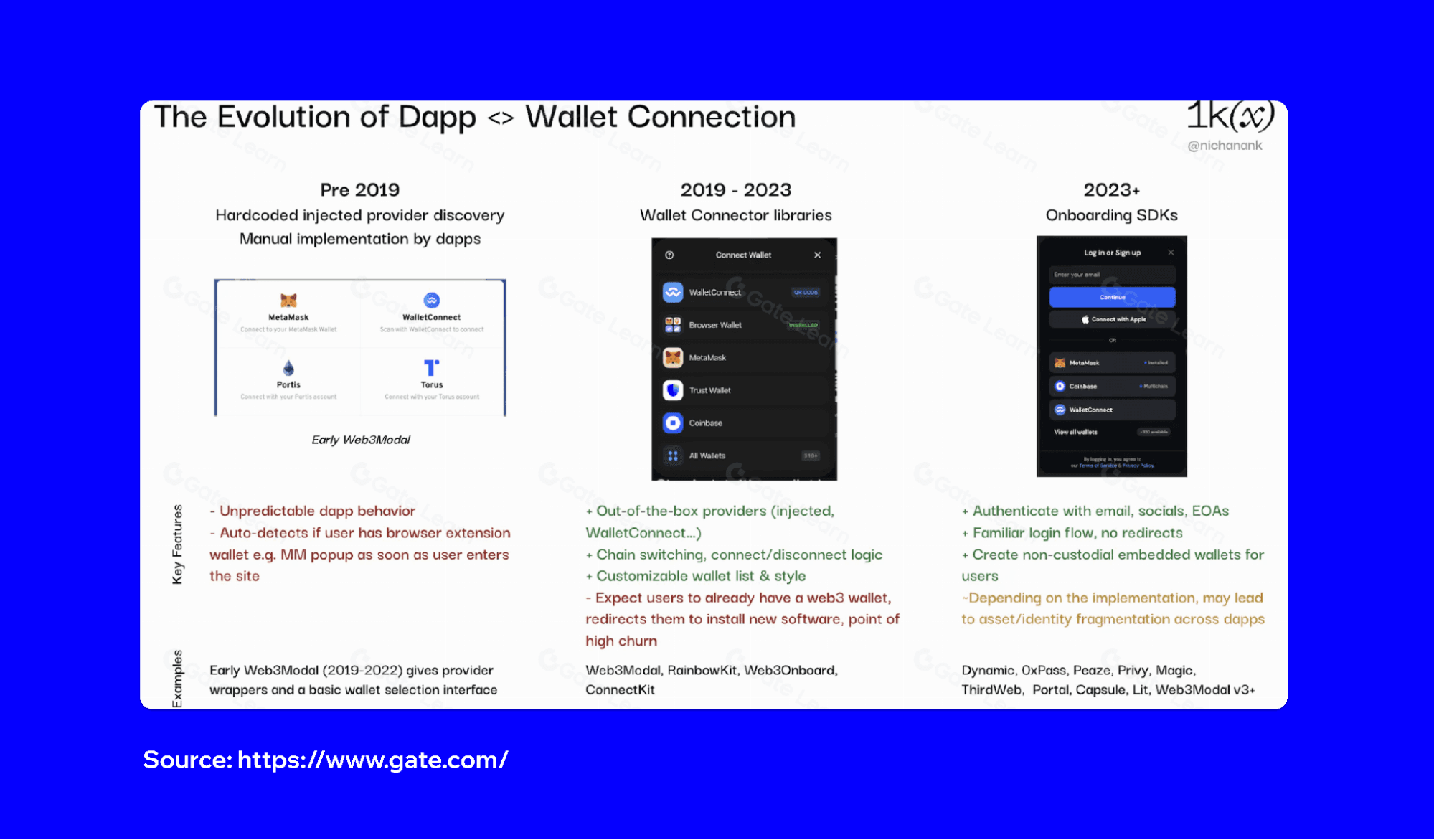
The risks of embedded wallets
An embedded wallet is built directly into a DApp, which means you do not need to connect an external wallet or manage private keys manually. Embedding the wallet makes onboarding easier, but it also changes where control and responsibility sit.
The biggest risk is private key management. An external wallet like Trust Wallet leaves key storage completely in your control. An embedded wallet, however, may generate keys automatically and store them in the app itself or on a server. If security standards are not met, private keys can be exposed or stolen. The risk grows when DApps rely on browser storage or weak encryption.
Another issue is lack of user visibility. With an external wallet, every transaction requires explicit approval. Embedded wallets often sign transactions in the background. Signing transactions in the background can create situations where you are not fully aware of what permissions you have granted or what funds are at risk. A DApp could, intentionally or not, request broader access than necessary, making your crypto vulnerable.
Embedded wallets raise questions about recovery. If you lose access to your device or account, the recovery options may depend entirely on the DApp provider. Without a decentralized recovery path, the DApp becomes a single point of failure.
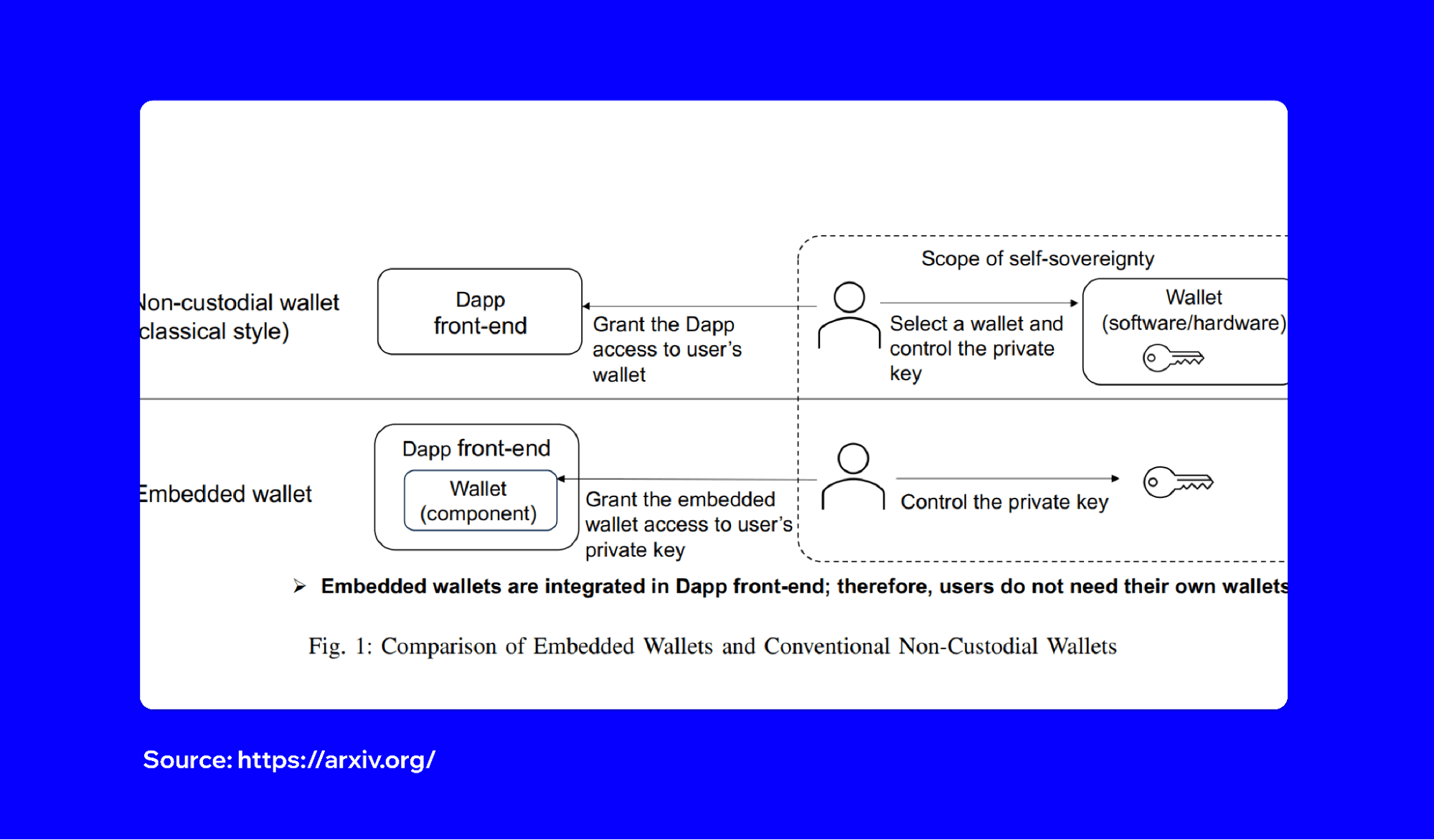
What the VELLET protocol shows us
VELLET is a lightweight protocol that improves how DApps manage embedded wallets. VELLET focuses on giving developers a clear framework for handling security while still offering ease of use for the end user. Studying the VELLET approach can teach key lessons about what embedded wallets should and should not do.
One of VELLET’s core mechanisms is secure key handling. Instead of leaving private keys in local storage or on a centralized server, the protocol enforces the use of strong cryptographic protections. VELLET makes sure that sensitive information never moves in plain text and always passes through audited processes.
VELLET emphasizes explicit consent. The protocol requires that every transaction request is made visible to the user with clear details. Explicit consent prevents silent signing and ensures that you can always verify what you are approving. VELLET encourages a trust-first approach by designing for transparency.
Another strength of VELLET is portability. Through its design, wallet states can be backed up in a secure, encrypted form. You are not locked to one device or platform. If one access point fails, you can restore your wallet without depending on a centralized recovery system.
In short, VELLET shows that embedded wallets can be safe if they follow strict rules. Embedded wallets must separate sensitive processes, always show the user what is happening, and never compromise on encryption.
Best practices for DApp integration
For developers building DApps, the lessons from VELLET and the risks of careless design point to several best practices.
The first is to ensure private key protection is at the center of the build. Keys must never be exposed to unencrypted storage or passed through insecure environments. Using hardware security modules or equivalent cryptographic protections reduces exposure. Developers should think of sensitive data as never leaving a secure boundary.
Total transparency is important. Every wallet action should be visible, and every approval must be explicit. Silent signing erodes user trust and creates unnecessary risk. Showing clear transaction details, even for small operations, helps people stay in control.
Developers must design clear recovery paths. A person should be able to back up or restore their wallet without relying entirely on the DApp operator. Options for secure backup, like encrypted exports, can balance independence with accessibility. Removing single points of failure gives people a safety net and protects against central failure risks.
Audits and testing should not be skipped. Independent audits of wallet code and protocols highlight weaknesses before they can be exploited. Continuous testing with security in mind sets strong DApps apart from weaker, less reliable ones.
When developers bring these practices together, embedded wallets can be used to improve access while respecting the security standards that the blockchain ecosystem depends on.
How to Create a Wallet Using Trust Wallet
Ready to start your crypto journey? Here’s a quick look at how to create a crypto wallet using Trust Wallet:
Download and install the Trust Wallet app from your device's app store.
Open the app and tap "Create a new wallet."
The app will generate a unique 12-word seed phrase for you.
Write down the seed phrase on paper in the correct order.
Verify the seed phrase by entering the words in the correct sequence when prompted.
Set a PIN or biometric lock for additional security.

Moving forward with safer embedded wallets
The push toward simple onboarding for DApps has made embedded wallets popular. Embedded wallets lower barriers but bring new security demands. Learning from protocols like VELLET shows us that embedded wallets must prioritize cryptographic strength, clarity, and decentralized recovery options. Developers who treat these as non‑negotiable principles can give people both convenience and safety.
Download Trust Wallet
Disclaimer: Content is for informational purposes and not investment advice. Web3 and crypto come with risk. Please do your own research with respect to interacting with any Web3 applications or crypto assets. View our terms of service.
Join the Trust Wallet community on Telegram, follow us on X (formerly Twitter), Instagram, Facebook, Reddit, Warpcast, and Tiktok
Note: Any cited numbers, figures, or illustrations are reported at the time of writing, and are subject to change.




