Güvenlik
Crypto Safety 2025: 7 Easy Ways to Avoid Hacks and Scams
Gönderiyi paylaş
Kısaca
Learn seven practical ways to protect your crypto from hackers and scammers in 2025. Simple security steps every wallet owner should follow.

Key Takeaways:
Strong passwords with biometric locks and offline seed phrase backups form the foundation of your crypto security.
Regularly review and revoke unused token approvals to minimize your vulnerability to compromised dApps.
Verify contract addresses manually. Watch for common scam red flags like pressure tactics and unsolicited messages.
Losing your crypto to hackers or scammers is one of the worst experiences in Web3. The good news? Most hacks and scams are preventable when you know what to watch for and take a few simple security steps. This guide walks you through seven practical ways to protect your digital assets. Whether you're new to crypto or have been around for years, these strategies will help you stay safe in 2025 and beyond.
Use a Strong, Unique Password Combined With Biometric or Device Lock
Your wallet's first line of defense starts with a password that nobody can guess. Avoid common passwords like "password123" or your birthday. Instead, create a password that mixes uppercase and lowercase letters, numbers, and symbols. Make it at least 12 characters long.
Never reuse a password. If a hacker gets your password from a data breach on another website, they'll try it on crypto wallets and exchanges. Each account needs its own password.
Always enable biometric authentication. Trust Wallet supports Face ID and fingerprint scanning on compatible devices. Your physical presence is required to access your wallet. If someone learns your password, they can't get in without using your fingerprint or face.
Set your phone or computer to lock automatically after a few minutes of inactivity. Automatic locking protects your wallet if you lose your device or if someone takes it while it's unlocked.

Backup Your Seed Phrase Offline
Your seed phrase is the master key to your wallet. The seed phrase can restore your entire wallet on any device. If you lose it, you lose access to your funds forever. If someone else gets it, they can steal your crypto.
Write your seed phrase on paper. Store the physical backup in a secure location like a safe or safety deposit box.
Don’t take photos of your seed phrase. Don't store your seed phrase in cloud services like Google Drive, iCloud, or Dropbox. Don't email it to yourself or save it in a password manager. Make multiple physical copies and store them in different secure locations. If one copy is destroyed, you'll still have access to your crypto.

Enable Watch-Only Accounts When Available
Watch-only accounts let you monitor your wallet's balance and transactions without exposing your private keys. Watch wallets are useful when you want to check your portfolio but don't need to make transactions.
In Trust Wallet, you can add watch-only addresses. You can track your holdings on your phone without the risk that comes from having the actual wallet credentials on that device. If your phone gets compromised, attackers can see your balance but can't move your crypto assets.
Watch wallets are a great option if you keep the bulk of your crypto holdings in cold storage but want to monitor them throughout the day. You get visibility without vulnerability.
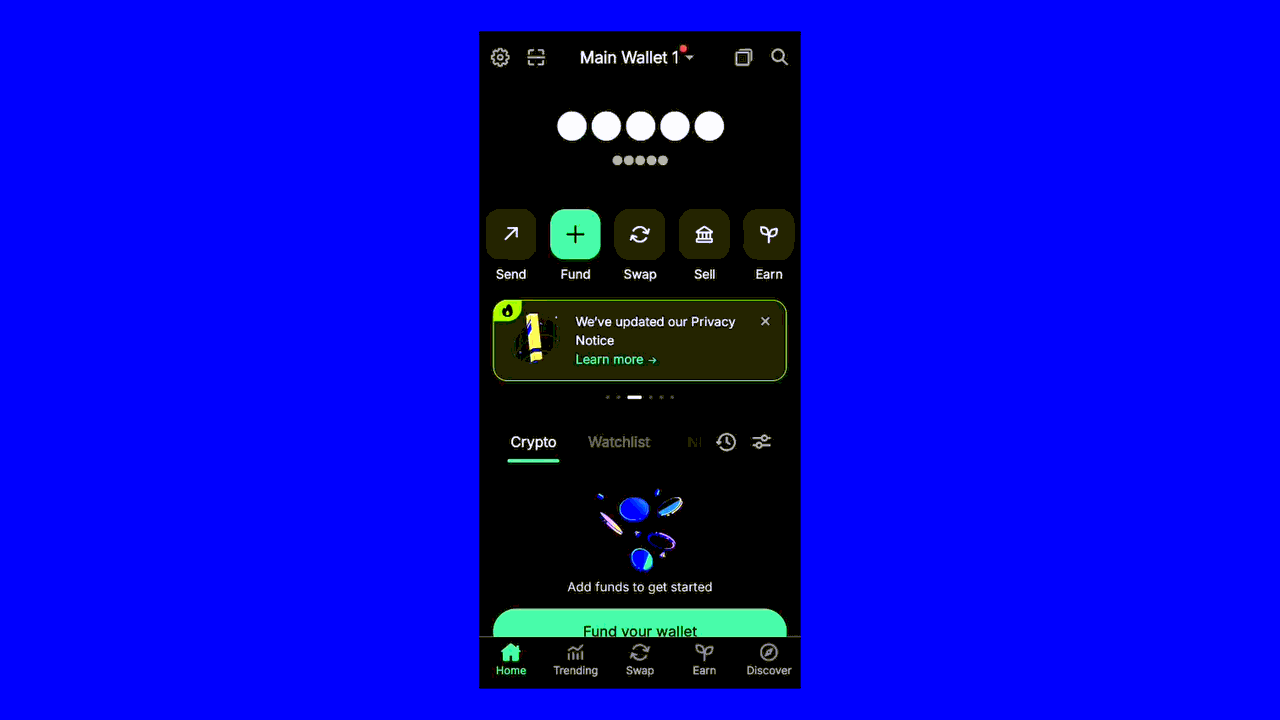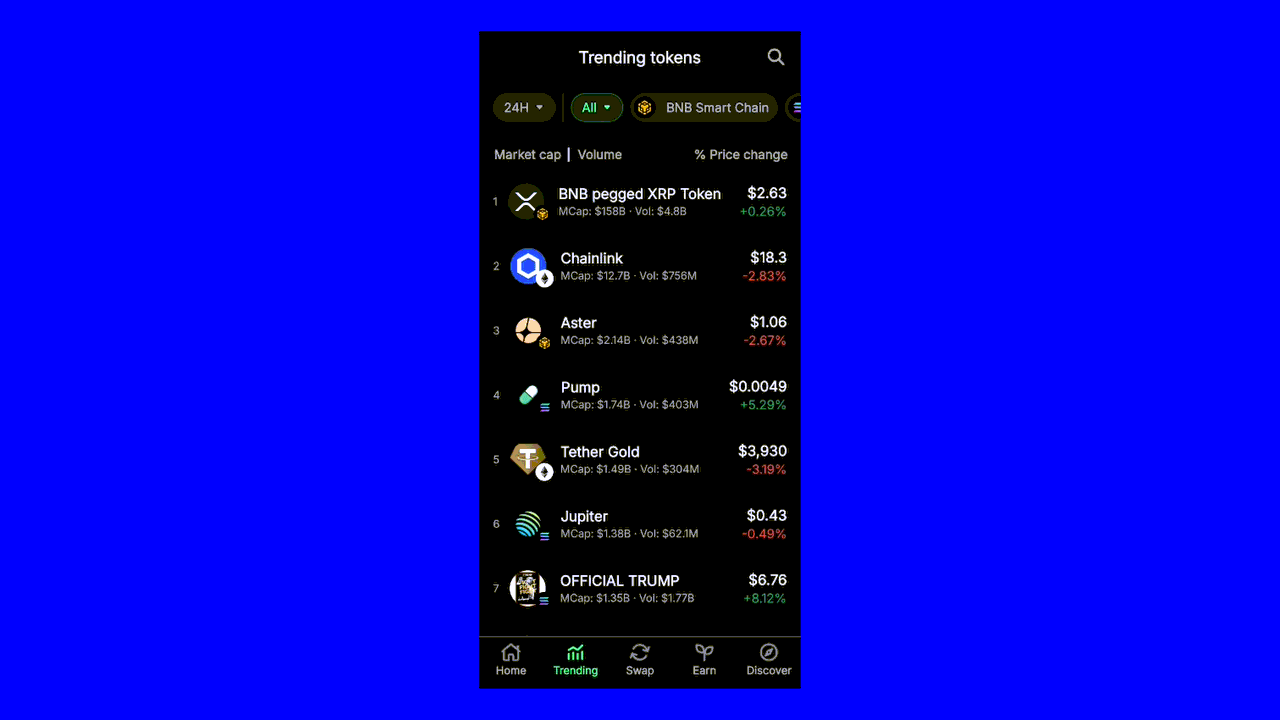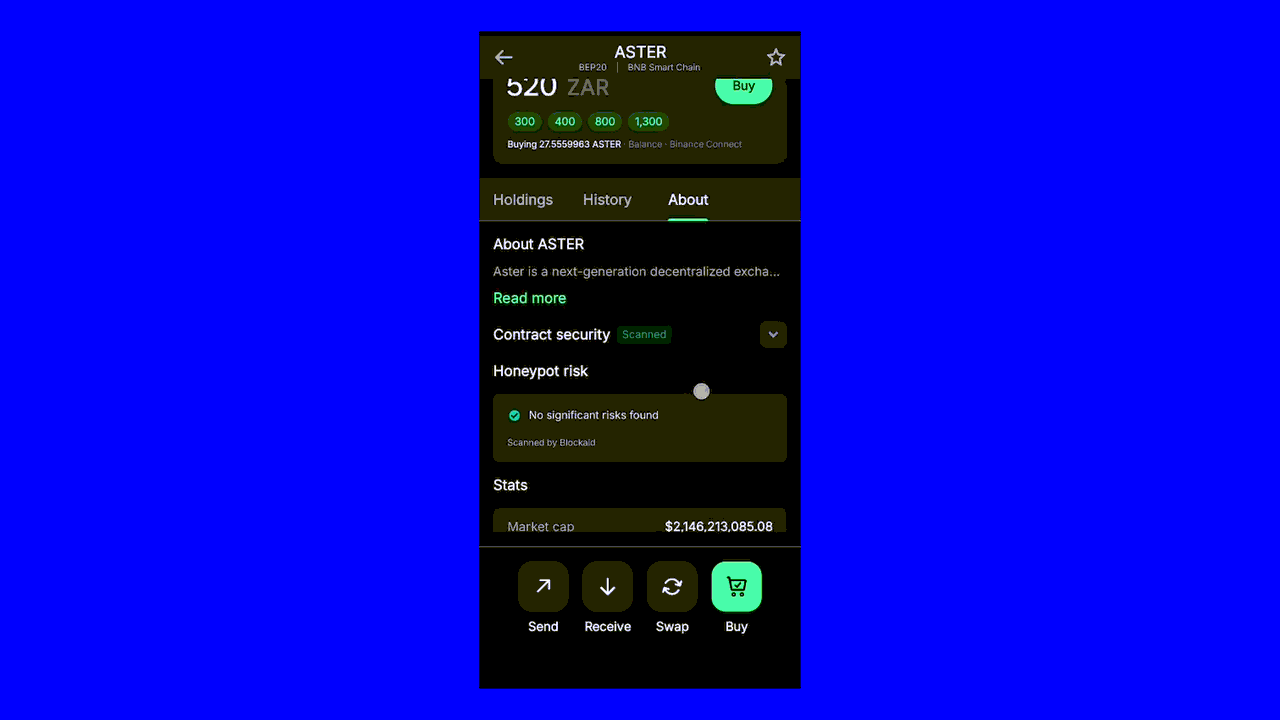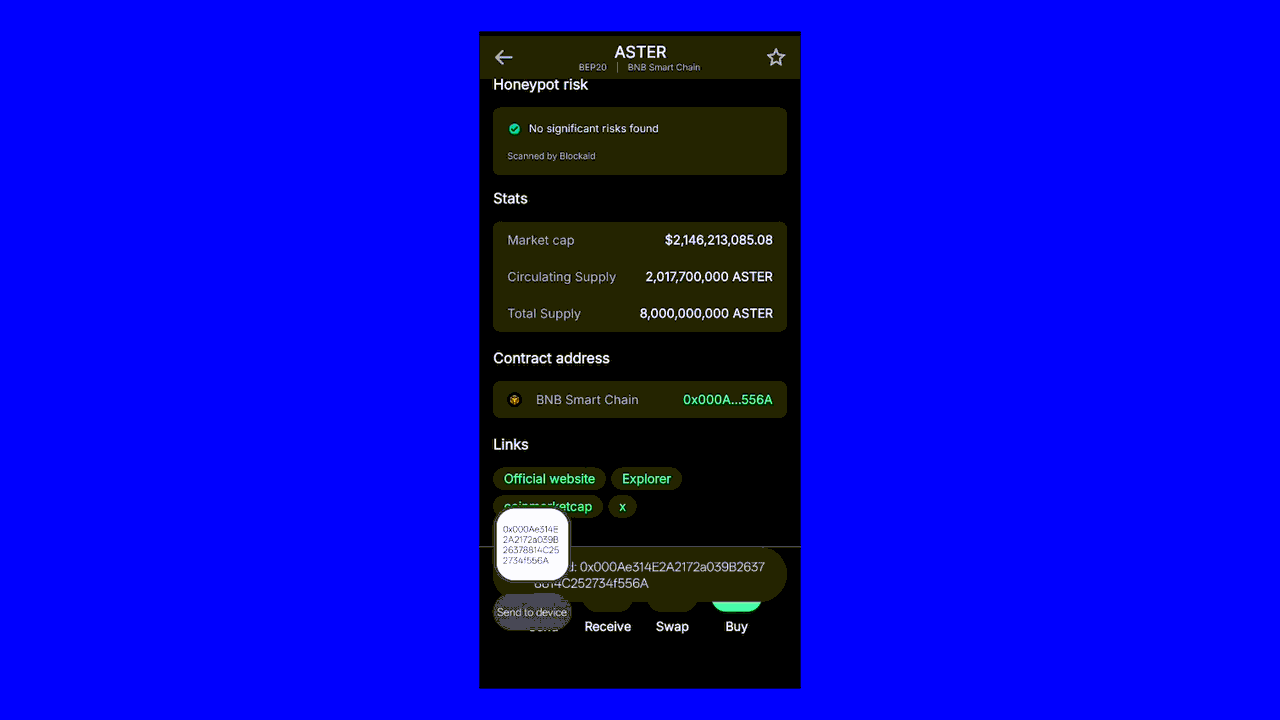
Verify Contract Addresses Manually
Scammers create fake tokens and malicious smart contracts that look legitimate. Before you interact with any token or decentralized application, verify the contract address yourself.
Go directly to the project's official website. Don't trust links from social media, Discord messages, or emails. Look for the contract address in the project's documentation or official channels.
Even one wrong character means you're looking at a fake. Scammers often create addresses that look like real ones, changing just a few letters or numbers. They count on people not checking carefully.
You can check a token’s official address in Trust Wallet. Here's how:
Limit dApp Allowances and Revoke Unused Token Approvals
When you connect your wallet to a decentralized application (dApp), you need to approve it to spend your tokens. Approvals stay active until you revoke them. Each active approval is a potential risk if that dApp gets hacked or turns out to be malicious.
Check your token approvals regularly using tools like Etherscan's token approval checker. You'll see every dApp and smart contract that can access your tokens.
Revoke approvals you no longer need. Revoking takes just a few seconds and costs you just a small gas fee. It’s worth it to keep your crypto assets secure.
When you do approve token spending, set specific limits rather than unlimited approval. Many dApps default to asking for unlimited access to your tokens. Only approve the amount you need for your immediate transaction.
Use Trust Wallet Backup and Recovery Features
Trust Wallet includes built-in backup and recovery features to protect your assets. When you create a new wallet, the app guides you through the backup process. Follow these steps carefully.
Trust Wallet encrypts your data on your device. Trust Wallet itself never has access to your crypto or seed phrase. You maintain complete control.
Test your backup before storing a large amount of crypto in your wallet. Delete the app and restore it using your seed phrase to confirm everything works correctly.
Keep your Trust Wallet app updated. Updates often include security improvements that protect against newly discovered vulnerabilities.
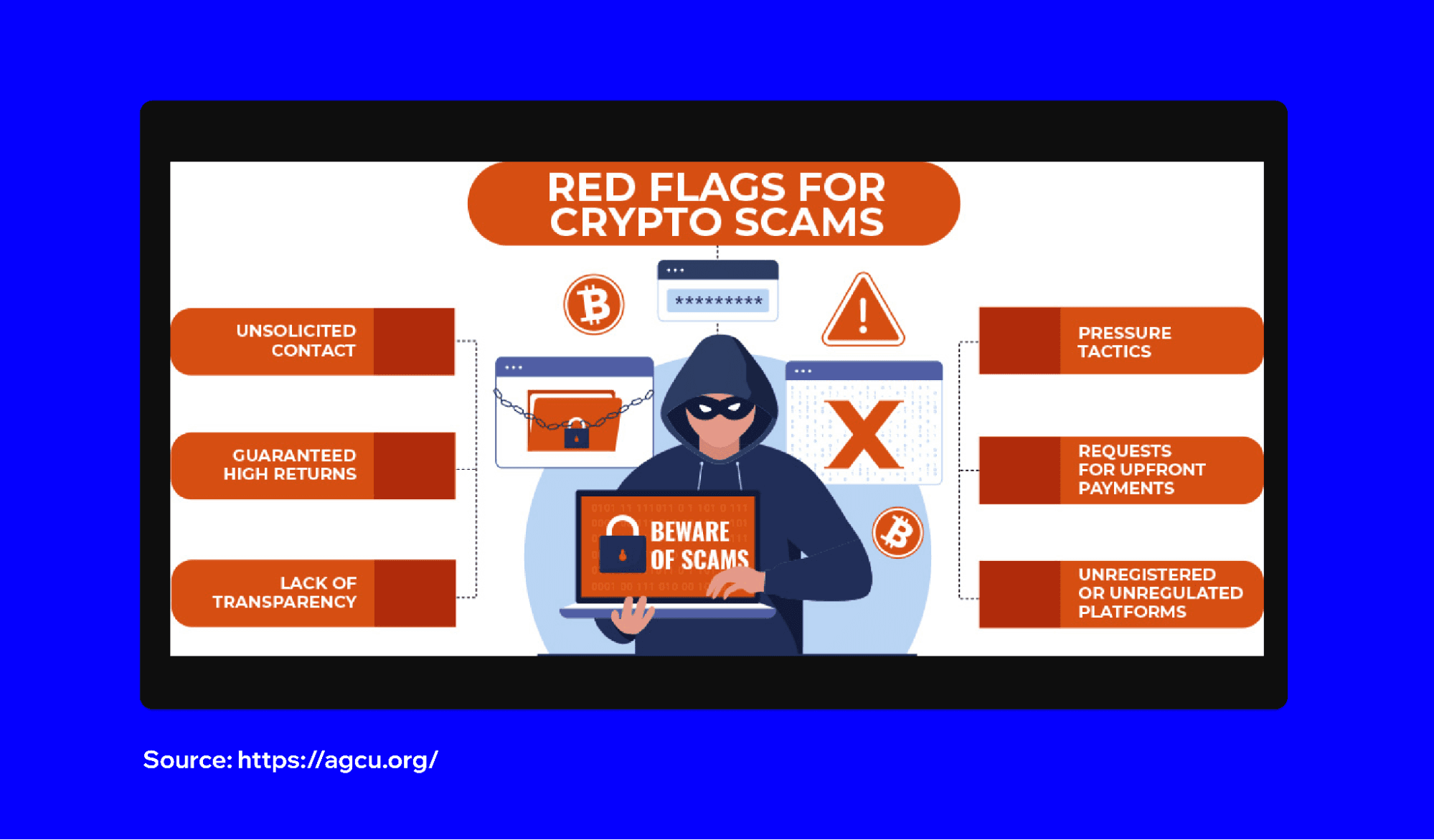
Watch for Red Flags and Common Scam Patterns
Scammers use predictable tactics. Be suspicious of anyone who contacts you first about an investment opportunity. Legitimate projects don't send unsolicited direct messages on social media or messaging apps.
If someone tells you an opportunity is ending soon or you need to act immediately, stop. Pressure tactics are used to make you skip security checks. Real opportunities will still be there tomorrow.
Promises of guaranteed returns or risk-free profits are simply not true. Any project making these claims is lying. High returns come with high risk, and nobody can guarantee profits in a volatile market.
Be wary of customer support reaching out to you. If you post about a problem on social media, scammers often reply pretending to be official support. They'll ask for your seed phrase or direct you to a fake website. Trust Wallet's real support team will never ask for your seed phrase or private keys.
Check for professional communication. Scam projects often have websites full of misspellings, grammatical errors and poor design. While not every legitimate project has perfect marketing, obvious quality issues should raise concerns.
Staying Secure in Web3
Protecting your crypto requires ongoing attention and good habits. The seven strategies in this article work together to help you create multiple layers of security around your assets. No single measure provides complete protection, but combining them makes you a much more difficult target for hackers and scammers.
The crypto space keeps growing and changing, bringing new opportunities and new risks. Stay informed about emerging threats by following trusted security researchers and official channels from the projects you use. Trust your instincts. If something feels off, take time to investigate before proceeding.
Your security is in your hands. Take these steps today, and you'll be doing your best to protect your digital assets.
Disclaimer: Content is for informational purposes and not investment advice. Web3 and crypto come with risk. Please do your own research with respect to interacting with any Web3 applications or crypto assets. View our terms of service.
Join the Trust Wallet community on Telegram. Follow us on X (formerly Twitter), Instagram, Facebook, Reddit, Warpcast, and Tiktok
Note: Any cited numbers, figures, or illustrations are reported at the time of writing, and are subject to change.




